Phishing is rife, and they’re only getting smarter
Hackers are desperately trying via a number of routes to get access to your private & sensitive data. Email is one of the simplest means of access for cyber criminals, with it often being the weakest entry point to a computer network.
Emails can of course be filtered, but unlike most other network points of entry, it can’t be blocked entirely, otherwise you wouldn’t be able to receive emails from anyone!
Phishing… is the word that explains the act of hackers masking malicious emails as a genuine message, through a few clever tricks. Their goal is to trick you into clicking on links embedded into email that may download viruses, malware, or worse, tracking software that’ll collect snoop around your device to capture your valuable data, such as your bank account login details.
How do they do it?
Masking emails as though they were sent from someone else’s mailbox is surprisingly simple to do.
The email itself, (in the majority of cases), isn’t dangerous. It can simply be checked & then deleted from your inbox.
If you have clicked the link & downloaded the file or opened the document, your computer is then open to be ‘hacked’ by whatever buggy software they intended to hit your machine.
See an example case below, (with the victim sender’s details omitted), to which we refer to through this blog article.
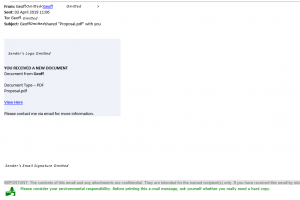
What does it look like in my inbox?
It’ll look just like a normal email in your inbox, alongside all of your genuine emails. So, at first glance, you’ll be none the wiser.
If the email is masked as though it is from a government department, it may well contain bad grammar or spelling, pixelated logos, or be requesting from you information that would normally be sent via the post or submitted via their secure websites.
The email is most likely to contain an attachment or a link, which is the lure to draw you toward their means by which they can enter your PC & steal your data.
What can I look out for?
When you receive any email there are a few key things to check, even if you know & trust the sender.
1. The sender’s name & email address. Does it match up and make sense? Has it arrived from their mailbox or does something about the name or email address not look right?
2. Does the email have an attachment?
If it is a PDF, there’s a strong chance that you’re safe.
If it is a Word or Excel document, it may contain a virus that can take over your machine as soon as you open it & activate any “macros” set to run within it. Always question and be wary of Word & Excel documents that you aren’t expecting. Invoices are an often seen trick used by the fraudsters – work by a rule of only opening invoices received as PDFs, that way you can be sure to avoid any hacks concealed within these Office documents.
One thing to bear in mind is that you can’t tell from looking at the file whether it is genuine or malicious before you open it. If you do open it and it’s malicious, it’s probably too late.
3. Does the email contain any links?
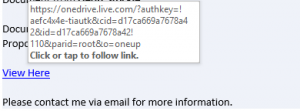
Links are a little simpler to check. Hover over the link and you can see the destination where it’ll actually take you.
If it’s an email purporting to be from HMRC or your bank, and the link wants to take you to a completely different non legitimate website address, don’t click on it!
If the link appears to be the real website, or where you would expect to land, like in the example below, then it may well be genuine, but that is no guarantee!
With this example, the link takes you to a file hosted on a Microsoft OneDrive account. The email makes it look like this user genuinely wanted to send you this file, which is hosted in a reputable place. If the link appeared to be of an untrusted source, it would appear to be more suspicious, but on face-value this particular link appears to be legitimate.
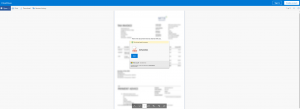
Clicking the link to visit the website, which appears to be a real Microsoft OneDrive file share, you can see an overview of the document, apparently a PDF.
Upon further inspection, hovering over the preview shows the Microsoft branded box with the “Open” link to infact just be an image, with the entire screen overlaid with a hyperlink to a shortened website URL via tinyurl.com. This cleverly masks the ultimate website address, likely a malicious website.
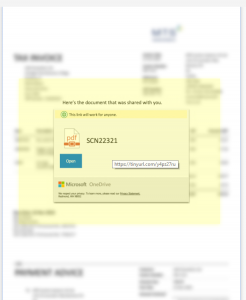
Had the “Open” button been clickable, like a normal website button, and the document been able to be viewed within the browser it would have likely been genuine. However, clicking this link does actually take you through to a virus riddled website, leading to the recipient’s email accounts vulnerable to being hacked & in-turn become a sender out the very same email I received.
In Summary
Be very, very wary. Even if you believe to know the person that sent you the email.
Follow our straight-forward 3-step check list – sender’s name & email address, attachments and links. Checking these three key things before taking any action with the email will help you remain protected.
Need some support for peace of mind?
We can help. We offer free assessments to businesses across the North East, from our home in Durham.
Omnicom Solutions provides a full range of professional IT services, including a full suite of cyber security products, including support with Cyber Essentials and aiding compliance to GDPR from a technical perspective.
Please contact the team today on 0191 386 6222 or solutions@omnicomsolutions.co.uk.

